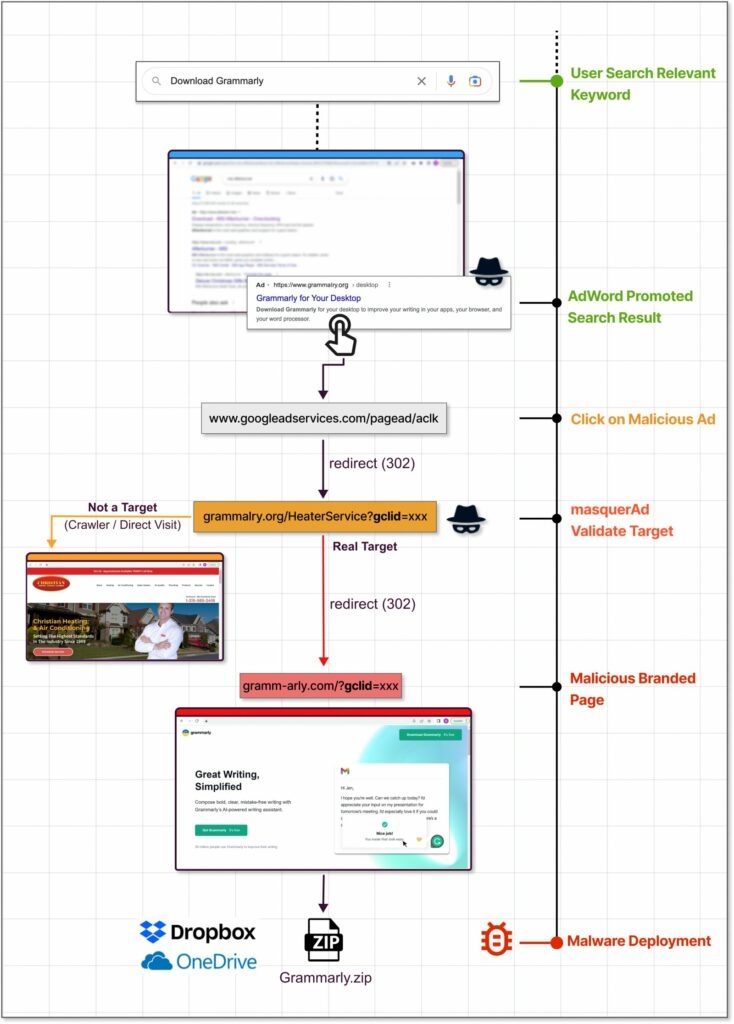
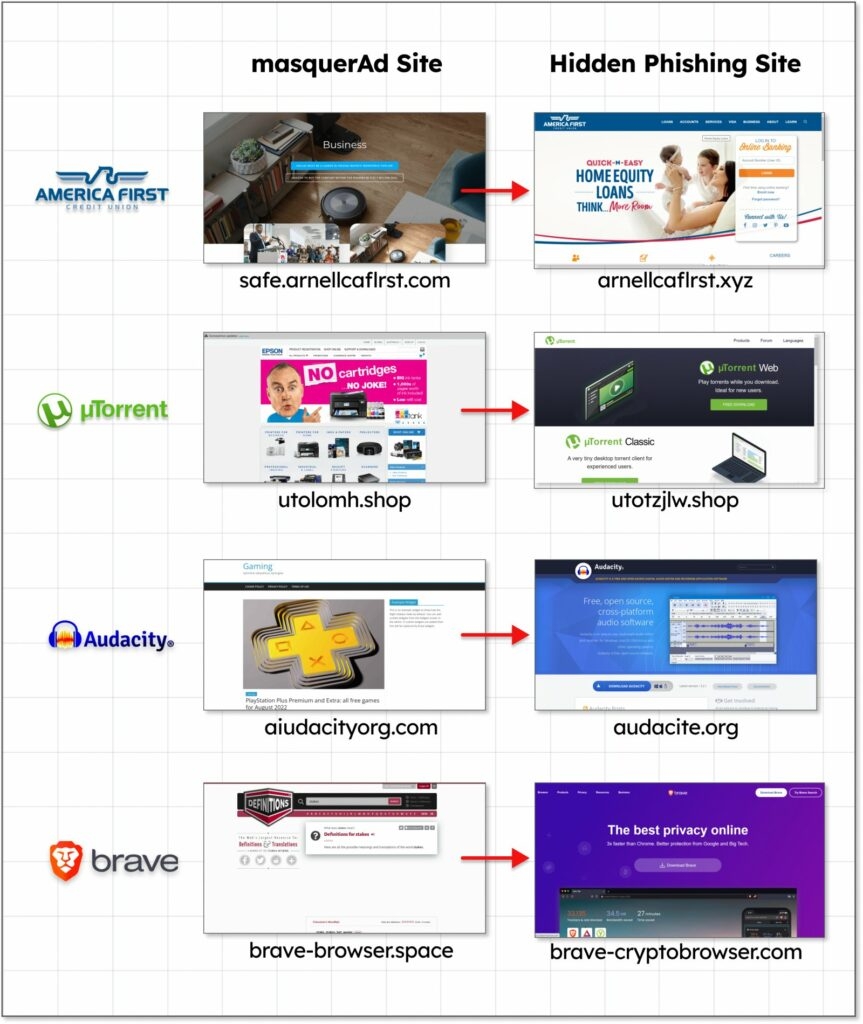
Well, the threat actors replicate the official websites of these software products and then spread trojan-filled versions of these products when the user clicks on the download button. These are the software products that the threat actors are targeting – Grammarly Malwarebytes, μTorrents, AnyDesk, MSI Afterburner, Slack, Thunderbird, OB.S, Ring, Libre Office, Brave, Dashlane, Teamviewer, and Audacity. Well, some of this malicious software that the victim got in their computers include the variants of Racoon Stealer, which is a custom version of the Vidar Steeler and the IceID malware loader. A month ago, we covered the MSI Afterburner campaign, which infected users with the RedLine malware, and a report by Bleeping computers mentions a massive typosquatting campaign in which up to 200 domains copied software products. It wasn’t clear how the victims ended up landing on those websites though reports from multiple security firms like TrendMicro and Guardio Labs explain that all that happened as the threat attackers got to the broader user base by promoting their websites via running Google Ad campaigns! Google ads platform is a service that lets advertisers promote their websites and pages while placing them at the top of the search and often above the official websites of the products. This means that the users who do not use or have ad blockers turned off will see that promoted website upfront and will click on them, taking them as an actual search result! The threat actors then apply tricks to bypass Google’s automated checks, and if Google finds out that the landing page is malicious, then the Ad campaign is blocked, and the Ads are removed. Now, as per GaurdioLabs and TrendMicro. The trick that the threat attackers use is to get the victims to click on the Ad and then take them to an unrelated but not harmful website, which by the way, is also created by the attacker from there, redirecting them to the malicious website impersonating the software product. So as soon as the targeted users visit the duplicate website, then the server immediately redirects them to the rogue website and from there to the malicious payload, said GaurdioLabs. Furthermore, these rouge websites are not even visible to the visitor, not reaching them from the real promotional flow, irrelevant websites to the crawlers, occasional visitors, bots, and Google policy enforcers. The Payload comes in a ZIP file and is downloaded from a legitimate website like GitHub, Dropbox, or Discord CDN, ensuring that the anti-virus running on the target computer won’t object to the download. According to the security firm, the campaign that they discovered in November in which the threat attackers attracted the users to the trojan-filled version of Grammarly, which had Racoon Stealer. The malware came with the original software, so the users get the legitimate software as well as the malware which would install silently. Coming to a report by TrendMicro explains that the IceID campaign in which the attackers exploited the Ketaro traffic system to detect if the user visiting the website is really a victim or a researcher, and then the redirection takes place; this TDS exploit has been there since 2019. Well, with that being said, the promoted search results are often difficult to identify as fake due to them carrying all the legitimacy elements so one way to block these ad campaigns is to activate an ad blocker on your browser, which will, in turn, filter out the promoted search results. Another way is to scroll down the webpage till you see the domain of the software product that you are looking to download. Read: RisePro Malware Stealing Passwords, Credit Card Info & Cryptocurrency Wallets